"Can my employer force me to download software onto my personal device?" This is, surprisingly one of the most frequently googled questions regarding employer demands. It highlights the first of many grey areas that come with BYOD. Whilst the benefits of BYOD for both employer and employee are undeniable, a BYOD policy is not without risk and when it comes to accessing business-critical applications on mainframes, IBM I and Unix, this risk needs to be managed.
At a time when remote working and BYOD is booming, employers are struggling with security requirements, auditing, use policies administration, reimbursement, employee satisfaction and productivity. Grappling with questions of whether they have to pay employees to ‘rent’ the portion of memory their app requires. Or whether they can really prohibit employees from accessing high risk websites on their own devices? What about where they can leave their device, who they can let use it or how often they have to update their software? The benefits of BYOD policies are considerable, with core savings estimated at $350 per employee, per year and estimated productivity gains of 81 minutes per employee, per week. So how can organizations set-up their terminal emulator to allow them to safely deploy and administer BYOD access, without risking security, employee morale, or business efficiency?
Application, or not
Not all emulators are created equally when it comes to BYOD suitability. Some emulators require specific application downloads on each device, with different versions for Android, and Apple. Other emulators require a Java or Active X plugin, and some will only function on certain internet browsers, desktop machines, or via a virtual desktop solution.
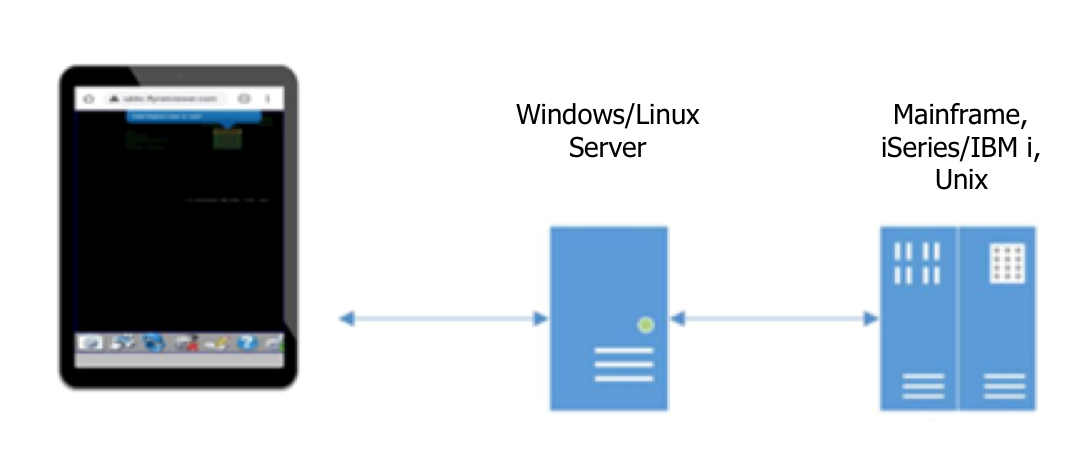
Ensure that whichever emulator you choose, it is truly zero-client and works on as many devices as possible, ideally all of them. The two methods have a distinctive impact on security, administration, cost, employee perception and adoption. It’s the difference between, "you can also access this application via whichever device is convenient to you, just visit this URL and authenticate as normal$quot; and "please download this application to your personal device. When you receive the bill, please send it to accounts for reimbursement." One is an option likely to increase employee productivity, the other is a demand that increases employer responsibility and a negatively impacts employee morale.
Security
When dealing with employees' personal devices, organizations will always have less control. It’s not reasonable to expect to be able to limit the other sites accessed on the device outside of work hours, police where they leave their devices, or control which emails they choose to open and click on. Although 36% of organizations require employees to sign a document giving the organization some control over their personal devices, the key to secure BYOD terminal emulation is reducing the threat surface on the actual device to as close to zero as possible. Ideally the threat surface would be removed entirely with a 100% browser based, zero-client solution. This helps to manage the security risk of lost, stolen and poorly wiped devices.
All security methods should be administered centrally around the application server and should not impact the native security on the mainframe, IBM I or Unix. Choosing an emulator that supports single sign on and multi-factor authentication, will further improve security for the end user. Other considerations are robust audit logging and ensuring the chosen solution does not rely on any third-party plugins.